Cloud data protection
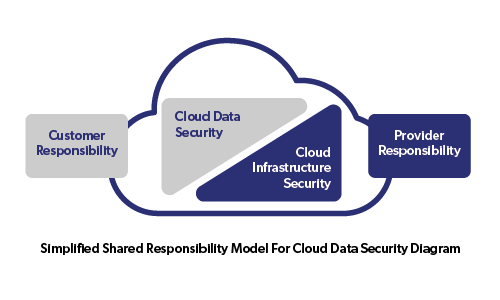
The well-established shared responsibility model for cloud security says that you are responsible for securing your data in Infrastructure-, Platform, and Software-as a Service (IaaS, PaaS and SaaS) environments. It’s a multi-cloud world, and Thales can help achieve full cloud data security.
The CipherTrust Data Security Platform, Luna General Purpose and payShield Payment HSMs, cloud based security services with Data Protection on Demand, Thales High Speed Encryption (HSE) network encryptors, SureDrop and Thales's SafeNet Trusted Access enables nearly any cloud environment to be a trusted and compliant environment by solving the critical challenges of data governance, control, and ownership.
Understanding the problem
The shared responsibility model for cloud security exists because in spite of the convenience, cost-savings, and even centralizations of IT expertise in the cloud, data breaches in and from the cloud are real. But why do breaches in the cloud happen? The answers can be found in several, preventable ways:
- Human error can still occur, perhaps exacerbated by self-service and varying security controls across different IaaS/PaaS and SaaS providers. Multi-cloud means learning new policies and cloud- and identity-security solutions.
- Vulnerabilities happen in software, hardware and firmware, whether on-premises or in the cloud. A breach of customer data from a cloud data store in 2019 was caused, in part, by a bug identified in 2015 and not patched in the cloud1.
- Insiders include both cloud infrastructure administrators plus your administrators with elevated privileges in the cloud. In IaaS, OS root users have too much visibility, with admin credentials targeted and compromised – sometimes the same passwords used in the cloud as on-premises. And with certain types of encryption, privileged users can see data in the clear for all users.
- Even with encryption, there remains the risk of poor practices for encryption keys, which truly require enhanced control and separation between encrypted data in the cloud and the keys.
These factors were confirmed in analyst research: an IDC study found that 61% of cloud data breach victims indicated that the breach was the result of a cloud or cloud infrastructure related vulnerability or misconfiguration2.
1Krebs on Security, August 2019
2IDC, Market Analysis Perspective: Worldwide Data Security, 2019, doc #US44772819, September 2019
Thales Wins Google Cloud Partner of the Year Award
Thales recognized as Partner of the Year in the
Security – Data Protection category
Thales helps you secure your cloud data
Cloud data protection can appear challenging at first, especially given the factors denoted above. Thales can help break security silos with a suite of integrated security solutions.
Centralized Cloud Authentication and Access Management
SafeNet Trusted Access ensures that only validated and authorized users can access sensitive data and apps in the cloud. Read about how we prevent data breaches and help organizations comply with regulations to secure access to cloud properties across IaaS, PaaS and SaaS.
Access Comes in Many Forms
Address a broad range of use cases by selecting from a broad range of authentication methods. Select authenticators based on your specific risks, risk appetite, and regulatory need. You can rely on hardware authenticators that are tamper-proof and clone-proof, manufactured in an environment in which the full development and manufacturing chain is tightly controlled. You also have the option of software authenticators to differentiate the types of users, applications and use cases to achieve differentiated risk management that you need for complex security needs.
Discover, protect and control
The CipherTrust Data Security Platform enables you to discover sensitive data in the cloud, protect it with encryption and tokenization, and control all encryption keys associated with data protection.
Go cloud-native with security
You can rearchitect your applications for the cloud while providing both data encryption and secure key management using CipherTrust Application Data Protection, a component of the Data Security Platform. With C, C#, Java and REST bindings to Crypto Service Providers (CSPs) located where you deem appropriate, PaaS data can remain secure.
Ensure you can trust your apps and data by securing the keys
Thales Hardware Security Modules (HSMs) provide uncompromised trust across cloud, on-premises and hybrid environments. HSMs safeguard digital identities, applications and sensitive key materials that are used to protect important collaboration tools, document sharing and online transactions. Meet your business and compliance needs securely and efficiently, as Thales HSMs provide a high assurance, FIPS certified root of trust for any use case, any application, any industry, delivered as-a-service in the cloud or on-premises, and across hybrid environments. Leverage Thales HSMs - Thales Luna General Purpose HSMs or Thales Luna Cloud HSM services from Data Protection on Demand (DPoD) and payShield Payment HSMs to ensure security.
Secure data as it transits the cloud
Today’s network encryption devices must handle intensive encryption algorithms, operate across a diverse range of cloud architectures and connectivity and be future proof against emerging threats. With Thales High Speed Encryption (HSE) network encryptors, companies can secure data in motion across network traffic between data centers, headquarters to backup and disaster recovery sites, in the cloud or on-premises.
Secure file sharing without compromise
Store, share and sync all your files in the cloud, or on premises, securely with SureDrop®.

451 Research Business Impact Brief “Native vs. Third Party: Who Should Deliver Cloud Security?” - Analyst Report
One of the core reasons organizations migrate to the cloud is its ability to simplify various operations and improve business agility – although this is often not the case for security. According to 451 Research’s latest Voice of the Enterprise: Cloud, Hosting &...

Owning your own Access Security - White Paper
The latest cybersecurity incidents affecting government agencies and organizations as well as large enterprises around the world, who have invested heavily in digital and cloud initiatives, have demonstrated the urgent need for a different approach to security. Based on cloud...

Thales HSMs Provide CredHub Security - Solution Brief
With the adoption of platform-as-a-service (PaaS) for the production of new cloud applications and services, businesses are bringing solutions to market faster, cheaper, and with lower risk than ever before. The Open Cloud Native Application Platform from Cloud Foundry gives...

Simplifying cloud access with SSO and contextual authentication - Fact Sheet
As enterprises adopt cloud applications, Single Sign On (SSO) is becoming very popular. As users are plagued with password fatigue, the never-ending burden of creating and maintaining separate identities and passwords for the multiple cloud and web apps they need to access on...

Best Practices for Cloud Data Protection and Key Management - White Paper
This paper describes security best practices for protecting sensitive data in the public cloud, and explains concepts such as BYOK, HYOK, Bring Your Own Encryption (BYOE), key brokering and Root of Trust (RoT). It explains the level of data protection that can be achieved by...
Best Practices For Secure Cloud Migration - White Paper
This white paper is intended to aid readers in forming a cloud security strategy and data migration plan when adopting public cloud services. Security Guidance Version 4.0 from the Cloud Security Alliance offers mature recommendations for those looking to adopt public cloud...

