The pentester's Swiss knife
Kerbeus-BOF Beacon Object Files for Kerberos abuse. This is an implementation of some important features of the Rubeus project, written in C. The project features integration with the C2 frameworks Cobalt Strike and Havoc. Ticket requests and renewals asktgt...
GitGuardian Shield: protect your secrets with GitGuardian GitGuardian shield (ggshield) is a CLI application that runs in your local environment or in a CI environment to help you detect more than 300 types of secrets,...
Catalyst Catalyst is an incident response platform or SOAR (Security Orchestration, Automation, and Response) system. It can help you to automate your alert handling and incident response procedures. Features Ticket (Alert & Incident) Management...
What is WHAD? The cybersecurity community has published a lot of wireless hacking tools based on various hardware platforms and custom communication protocols specifically designed to work with associated software. This leads to hackers...
betterscan-ce It is a Code and Infrastructure (IaC) and Cloud-native Scanning/SAST/Static Analysis/Linting solution using many tools/Scanners with One Report. You can also add any tool to it. Currently, it supports many languages and tech...
logdata-anomaly-miner This tool parses log data and allows to definition of analysis pipelines for anomaly detection. It was designed to run the analysis with limited resources and the lowest possible permissions to make it...
Power Pwn An offensive security toolset for Microsoft 365 focused on Microsoft Copilot, Copilot Studio and Power Platform. Modules: Copilot Connector and Automator Allow interaction with Copilot for Microsoft 365 through the WebSocket messages...
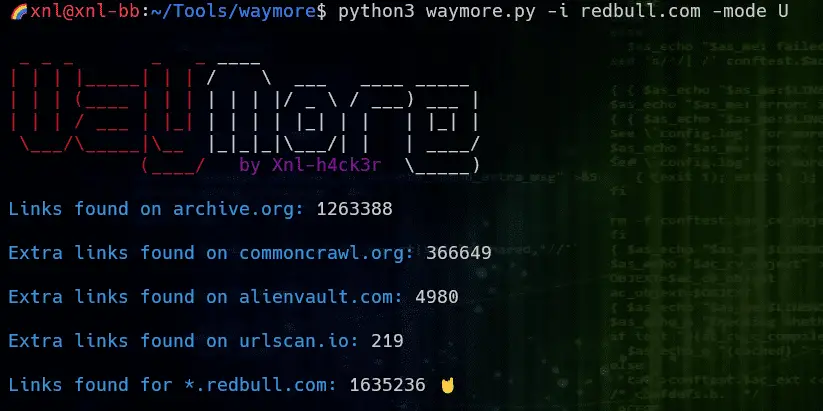
waymore The idea behind waymore is to find even more links from the Wayback Machine than other existing tools. 👉 The biggest difference between waymore and other tools is that it can also download the archived responses for URLs on...
Hubble Hubble is a fully distributed networking and security observability platform for cloud-native workloads. It is built on top of Cilium and eBPF to enable deep visibility into the communication and behavior of services as well as...
Bearer Bearer is a static application security testing (SAST) tool that scans your source code and analyzes your data flows to discover, filter and prioritize security risks and vulnerabilities leading to sensitive data exposures (PII, PHI, PD). We...
PyCript The Pycript extension for Burp Suite is a valuable tool for penetration testing and security professionals. It enables easy encryption and decryption of requests during testing, which can help evade detection and bypass...
Mageni Mageni is an open source vulnerability management platform. Mageni provides a faster, enjoyable, and leaner vulnerability management experience for modern cybersecurity programs. Real-life problems that Mageni solves for you Assets Discovery Services Discovery...
Nosey Parker: Find secrets in textual data Nosey Parker is a command-line tool that finds secrets and sensitive information in textual data. It is useful both for offensive and defensive security testing. Key features:...
Caido Caido aims to help security professionals and enthusiasts audit web applications with efficiency and ease. Feature Sitemap The Sitemap feature allows you to visualize the structure of any website that is proxied through...
Reverse SSH Want to use SSH for reverse shells? Now you can. Manage and connect to reverse shells with native SSH syntax Dynamic, local and remote forwarding Native SCP and SFTP implementations for retrieving files from your targets...
Grimoire Grimoire is a “REPL for detection engineering” that allows you to generate datasets of cloud audit logs for common attack techniques. It currently supports AWS. How it works First, Grimoire detonates an attack....