Hardening the Election Security: Supply Chain, Zero Trust and Insider Threats
Mandiant
Written by: Richard Alvarado, William Fecke
Some people envision election-related cyber attacks as a threat actor sitting in front of a keyboard in a windowless room trying to infiltrate voting machines while elections are happening. But, the reality is that election security is much deeper and more complex than protecting voting infrastructure.
Ensuring the integrity of our electoral system is not “questioned” is a tall order as it may come down to small details like verifying that enough paper ballots are printed and mailed out or that everyone working in our elections has been adequately trained and vetted.
Regardless of the scale or type of election—local, state, or even national- local and state officials bear the responsibility to secure this democratic process, making it more challenging to implement and enforce standardized security measures and procedures. Despite the effort it entails, we understand the importance of protecting the integrity of our electoral process and how cybercriminals or state-sponsored actors can disrupt our way of life by discrediting our elections.
Threats or attacks to our electoral system can also come from within our electoral system, whether intentional or something so simple as a slip of the finger when tallying up results that could bring into question the validity of the whole election process.
With the midterm elections around the corner, we present a holistic approach to making our elections more secure.
In this article, we will be discussing Supply Chain Risk Management, Zero Trust Philosophy, and Insider Threat Management. We have intentionally forgone examining the Chain of Custody, Access Control, and Standard Operating Procedures as these are mature components of the electoral process.
Modern Election Problems
In the past, supply chain risks to elections were typically comprised of risks of ballot availability, voting locations, and personnel to facilitate voting. This was demonstrated during the pandemic as the influx of mail-in ballots threatened the supply of paper ballots. Integrity was maintained through physical control that could be readily cataloged and captured through two-person integrity and other commands. Fraud, in general, was not scalable. Supply chain risks, in this sense, affected availability.
We introduce unforeseen complications as we move toward electronic ballots and voting systems. We now must consider that the methods we use to vote are compromised and the discovery of any compromise could prove difficult if not assessed. This new risk directly affects the integrity of elections. The new systems provide avenues to scale potential attacks that may not have been fully considered in the past. In this case, we introduced a new scalable risk to integrity. Because of the scale at which these systems are interconnected, this risk to integrity comes from two different sources, malicious and accidental.
After the 2020 elections, much has been said about the security of our electoral system. Regardless of varying views on the past election, we would all benefit if the Federal Zero Trust Strategy principles were applied to our electoral process. The Office of Management and Budget (OMB) published the Federal Zero Trust Strategy on January 26, 2022, to help guide agencies’ security architecture based on Zero Trust principles.
Potential Scenario
Imagine for a second that during the setup of the voting equipment, there were voting records from a previous election still on the machine. This poses a strange but frequent problem; the voting machine was not properly reset after the last election. We must consider if the old data poses an integrity problem for the election, or could the integrity of the current election be called into question even though the records are clearly from a previous election?
Electoral staff are required to receive, test, and install the voting equipment, but breakdowns can occur at several levels of this process so there must be checks and balances to ensure things are done correctly. This is where a holistic approach to election security can help.


Election security goes beyond technological controls or solutions; it’s a complete mindset that encompasses rethinking how and why we do everything and ensuring it is adequately documented and repeatable.
Supply Chain Risk Management
According to the Center for Internet Security (CIS) in their Supply Chain White Paper from 2021, managing the risks injected into your organization by your suppliers is part of managing the overall risks. The objective is to manage risk to an acceptable level. With that, how do we “manage” the risks of an outside organization?
The main objective of a proper supply chain risk management program is to build a close relationship with your vendors and ensure that you both work together to reduce any risk that may directly impact the elections. This can be an expensive and time-consuming endeavor, but very necessary. It was never so evident as when the SolarWinds Supply Chain attack was discovered; in this case, it was led by cyber criminals supported by the Russian state. It’s highly recommended that the Supply Chain Risk Management Framework be implemented to ensure a consistent and repeatable process is followed.
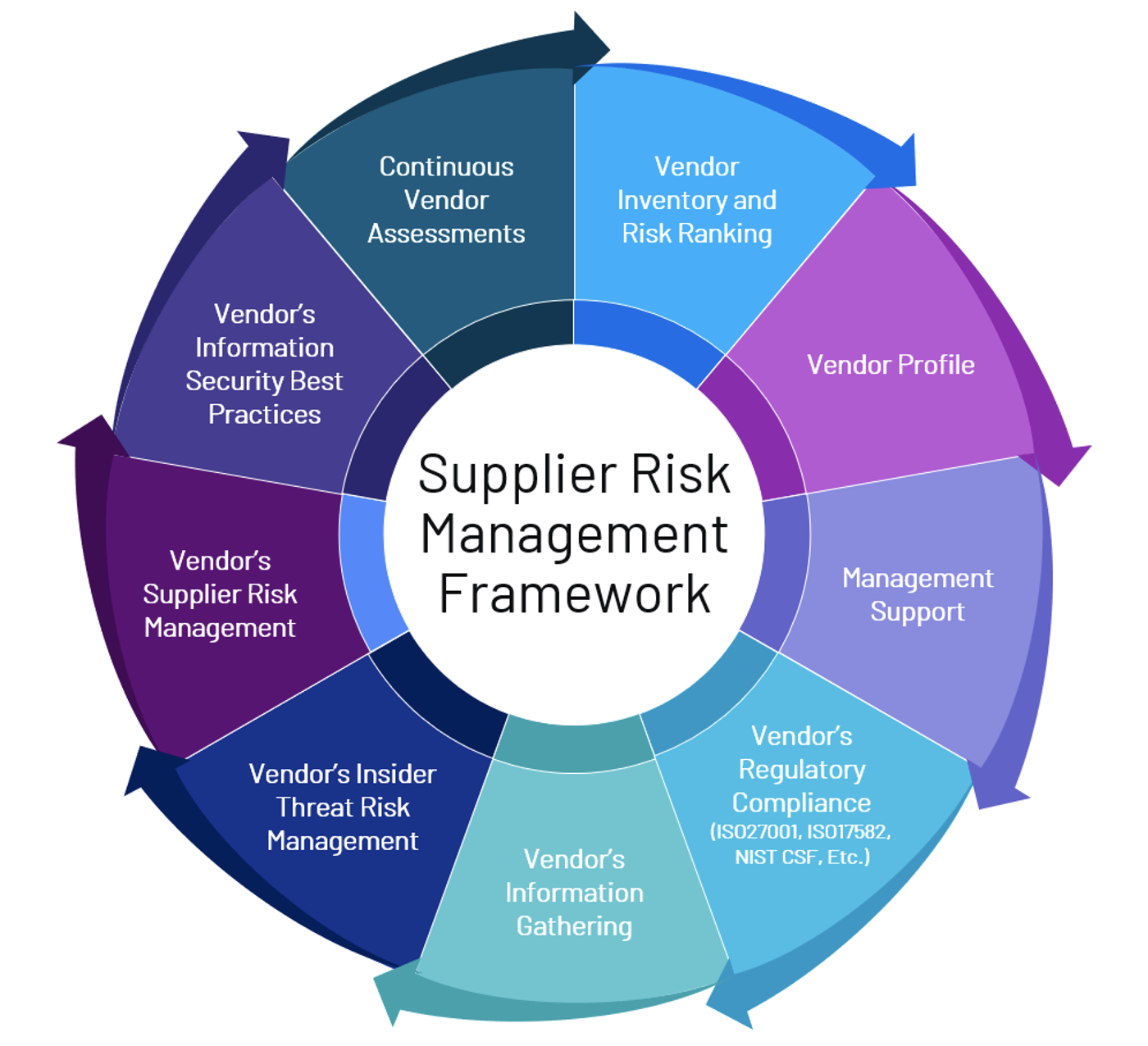

Using Zero Trust in Our Elections
The current threat environment demands that local and state officials address election cyber security risks at a holistic level rather than individually. This can be achieved by adhering to the Zero Trust principles.
Zero Trust principles can be summarized in “never trust, always verify,” so we will present how these principles can be applied in our electoral system. Cross-mapping Zero Trust principles to components of our electoral infrastructure can provide a more trustworthy electoral process. Below are several recommendations on where to implement these principles.


We are applying the principles of Zero Trust to these components of a modern election to help reduce risk and ensure the integrity of the election.
- Identity: Often, our first thoughts are of voter identity, but in this case, voters are only one part of an election. Vendors, contractors, and other entities are responsible for setting up, orchestrating, and supporting the election process. We need to verify the identities of these groups and clearly define what each is responsible for.
- Devices: Devices are any physical or virtual infrastructure to support the election process. If the equipment was tampered with or there is a lack of equipment, both pose dangers to the integrity of the election. If a chain of custody for equipment is established for the equipment, this allows us to understand our inventory and where it has been.
- Networks: Networks refer to how we interconnect devices to transmit electoral data before, during, and after an election.
- Applications: Applications refer to the applications, software, and firmware running on all devices used to support elections.
- Data: Data refers to any data used during the electoral process; this may be voter information, ballot data, voting results, etc. Data needs to be adequately safeguarded from tampering or disclosure.
This lengthy process is required to build a chain of trust necessary to hold successful elections, and each piece depends on the component to its left and right. Any failure in the chain fails in the entire election. Therefore, trust is so essential that we must verify every detail.
Insider Threats
Insider Threats to elections exist whether we decide to address them or not, and with this knowledge, election boards are compelled to address them.
Insider Threat is the potential for an insider (person with authorized access to or knowledge of the organization’s resources) to use their authorized access to harm the electoral process.
Insider Threat Categories
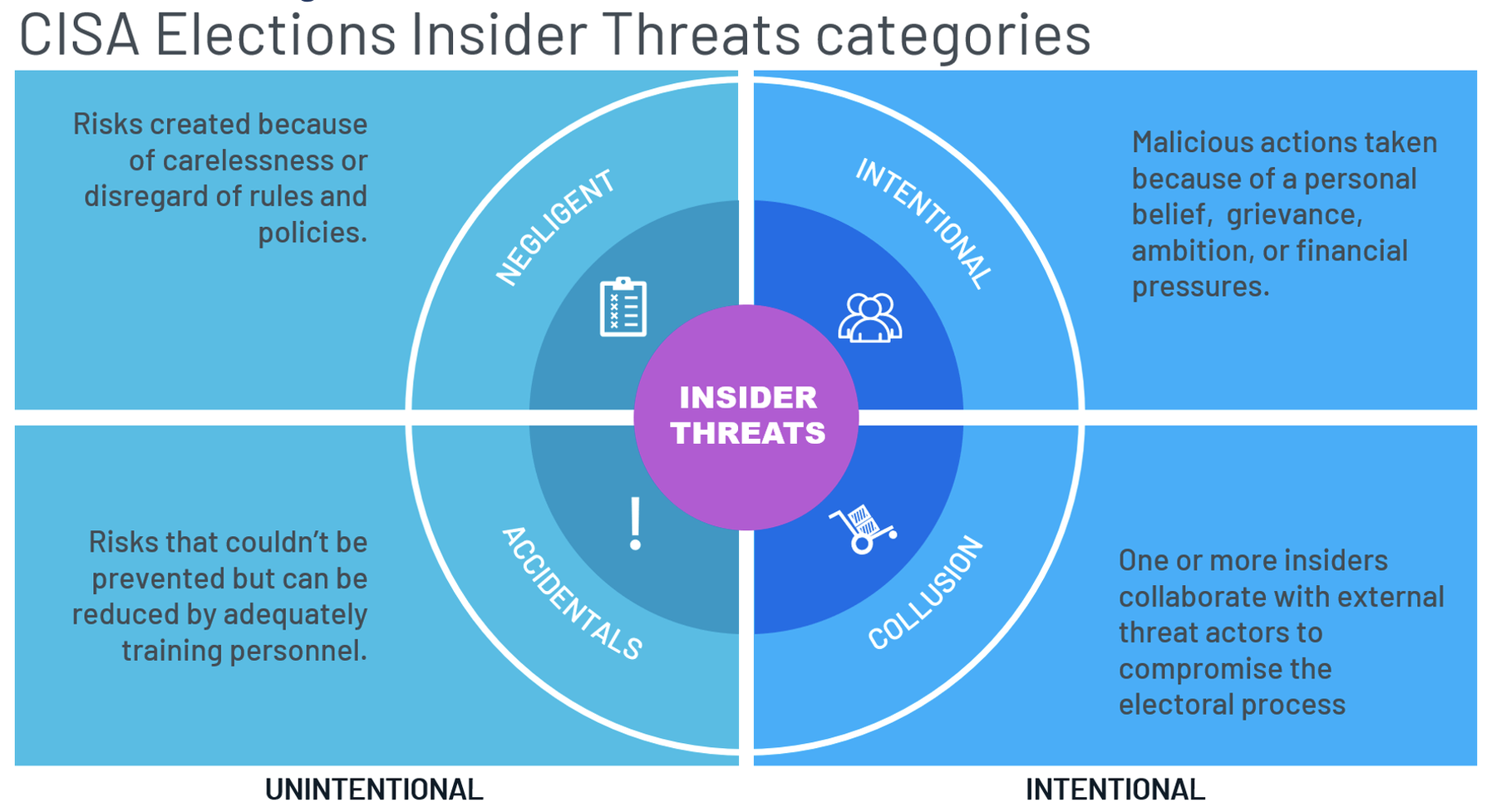

Risk management experts state that risks cannot be eliminated; we can only seek to manage them appropriately to a level that protects the electoral process and the staff supporting it.
Unintentional Insider Threats can be reduced by providing proper training, documentation, and controls for all procedures of the electoral process. It’s also valuable to keep a keen eye on the behavior and attitude of the electoral staff, as some negligent actions can be witnessed by others and corrected appropriately.
To address intentional Insider Threats, it is vital to understand the motivations of the individual that poses a threat. This is much easier said than done, as the motivations can be as varied as the gamut of human emotions. These motivations can include monetary gain, need for recognition, attention seeking, and a distorted image of what is right and wrong.
These motivations may lead electoral staff to collude between them or third parties, which can cause all sorts of harm, from spreading dis-misinformation or malinformation to breaking physical security protocols that can pollute or tamper electoral data such as ballots or poll books.
WHAT IS MDM, and why should we care?
CISA uses the following definitions for mis-, dis-, and malinformation (MDM). MDM can originate from both foreign and domestic sources.
- Misinformation is false but not created or shared with the intention of causing harm.
- Disinformation is deliberately created to mislead, harm, or manipulate a person, social group, organization, or country.
- Malinformation is based on fact, but used out of context to mislead, harm, or manipulate.
MDM can impact the perceived integrity of an election by influencing insiders and motivating them to take malicious actions. MDM must be addressed publicly, promptly, and not ignored, as its psychological effects are real and can cloud the decisions of electoral staff. It’s widely known that Russia has conducted MDM campaigns to discredit and question the validity of past elections. MDM tactics also look to foment a sense of belonging to groups and communities who consume this MDM as justification for malicious actions.
Addressing Insider Threats
Addressing Insider Threat requires a holistic approach incorporating components of the Zero Trust philosophy, Chain of Custody, Access Control, and proper documentation. Ensuring that Insider Threats are reduced is a daily task of election officials. It requires constant review and update of Insider Threat Management programs to adapt to the rapidly evolving MDM dissemination.
We must continue to protect elections’ integrity and availability by recognizing that it’s a complicated process. Mandiant can help State and Federal level authorities through the process of understanding these risk types and help develop the appropriate controls to mitigate them, maintaining the integrity and availability of the election. Ultimately, we must trust our election process, which means we must secure it.
